With revenue leakage to grey routes costing the A2P messaging industry $5.76 billion in 2018 according to Mobilesquared, more and more Mobile Network Operators (MNOs) are deploying SMS Firewall solutions.
However, merely installing an SMS Firewall is not enough to close revenue holes as MNOs continue to struggle with taking full control over international A2P traffic due to:
- Incomplete awareness of businesses generating A2P traffic
- Inability to monitor all the services and how they are currently delivering traffic
- Lack of direct connections to businesses who are generating A2P traffic
- Lack of an integrated team and effective procedures
Often MNOs don’t even suspect that they suffer losses
It is extremely important for MNOs to monitor SMS traffic in as detailed a way as possible. Even if an MNO monitors total daily A2P traffic volumes from international partners, it is impossible to understand the reason for traffic deviation. It’s good when mobile operators are able to monitor traffic from popular OTT services such as Facebook, Google, and WhatsApp.
Meanwhile, according to the traffic profiles in different markets, TOP services bring only 50-60% of overall volumes. Thus, dozens of other global businesses, generating international A2P traffic, escape their attention, although combined, they send huge volumes of messages comparable to OTT services.
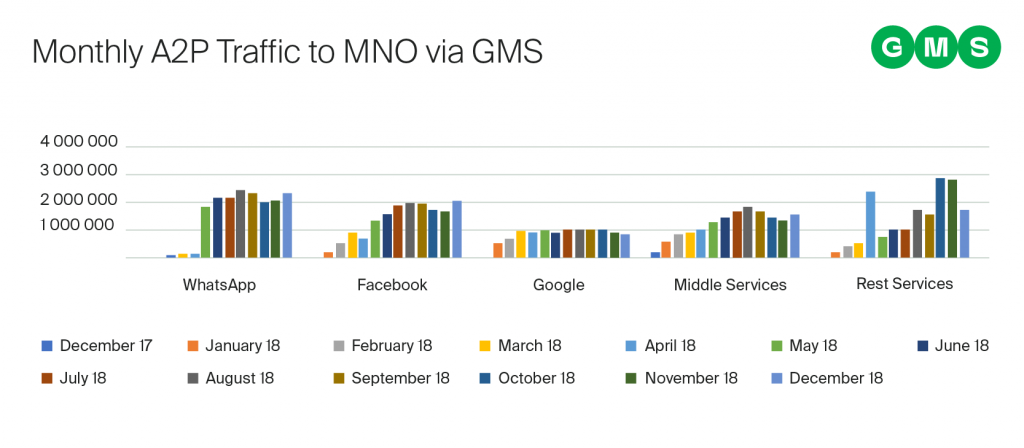
Traffic profiles in different markets show that OTT services bring only 50-60% of overall volumes.
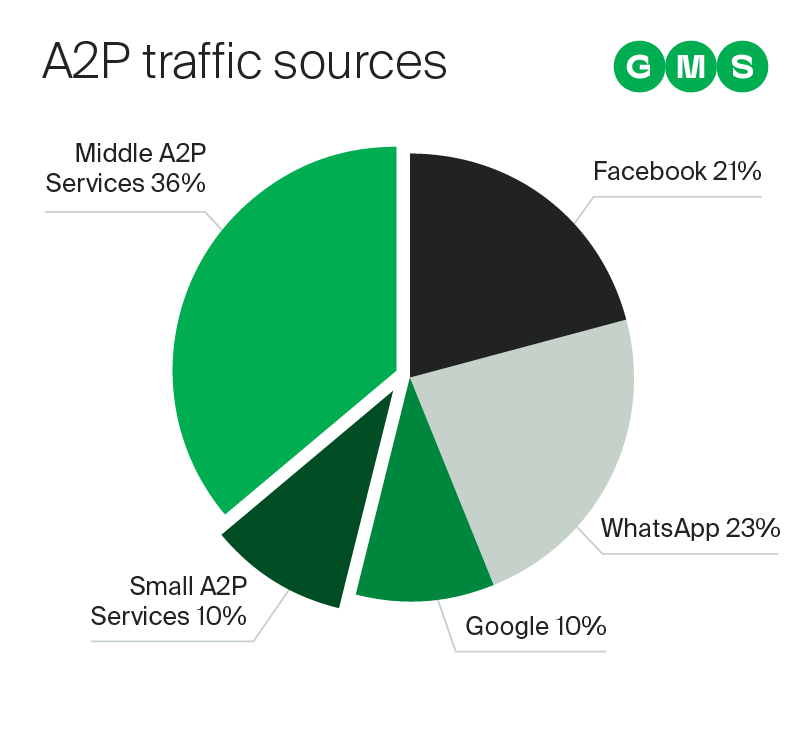
Up to 50% share of international messages in overall traffic might seem irrelevant to an MNO, but considering the huge difference in monetisation rates for global and local SMS traffic, revenue losses are heavy.
Know your network
Mobile operators will never really know where things stand until they have a comprehensive understanding of the international A2P market. To spot holes in their SMS Firewalls, the first thing for MNOs to do is to get to the bottom of international A2P messaging and gain proper visibility of all businesses sending A2P messages.
Sergii Sushchenko, Head of Pre-Sales Division
“The first thing an operator gets from working with GMS is a clear understanding of businesses generating international A2P traffic and real volumes of messages the operator should receive from them. If there is not enough traffic according to our calculations, then we immediately begin analysing where the leak is.”
Route all traffic to the single door
A2P traffic can flow into an MNO’s network through different channels: subscribers, local, international.
The difficulty for MNO lies in the fact that control of these channels is usually spread between different departments and the successful launch of a project demands an agreement between them all.
Ideally, all traffic must be unified and routed through a single SMS Firewall, regardless of the source: international A2P, international P2P, local P2P, local A2P.
MNO’s lack of control
Escaping an MNO’s control, a large amount of A2P traffic is delivered via grey routes.
Some mobile operators are even using scripts, algorithms, and machine learning to look into each traffic category. But they are still at the end of the data chain and can only see messages incoming to the network.
Regulators prohibit MNOs from reading the content of the messages. The problem is that even having the full knowledge of its A2P traffic, an operator can’t clearly understand in which cases enterprises interact with a user by SMS: it could be registration, password recovery, binding a phone number to an account, two-factor authentication password confirmation, etc.
Moreover, some services send different types of traffic (authorisation with OTP passwords, notifications, promos) and ability to control how this traffic reaches subscribers also brings benefits to both parties — OTT-service and mobile operator.
This lack of control on the part of an MNO means that a dodgy hub can take advantage of it — by sending only a small part of the traffic via an authorised channel, and the rest — through the cheap grey routes.
Therefore, it is mandatory for MNO to monitor if all expected volumes received in authorised A2P routes.
Cent by cent — MNOs are losing billions
Suppose there is some A2P traffic from Facebook to a mobile network operator. An opportunity to not pay high international rates for delivery and earn a couple of extra cents on a message creates a big temptation for a partner hub to insert a manipulation in SMS.
“Facebook” is not the same as “Faceb00k” — a simple change in the message text, like a zero instead of the letter “O,” will allow to bypass the standard set of rules on the operator’s SMS Firewall and deliver the message via an inexpensive P2P channel.
Another example of a message requested from Instagram with expected text pattern “Use 150 022 to verify your Instagram account. #ig” fully replaced into circled Unicode digits, delivered via local sim-box as domestic P2P SMS.
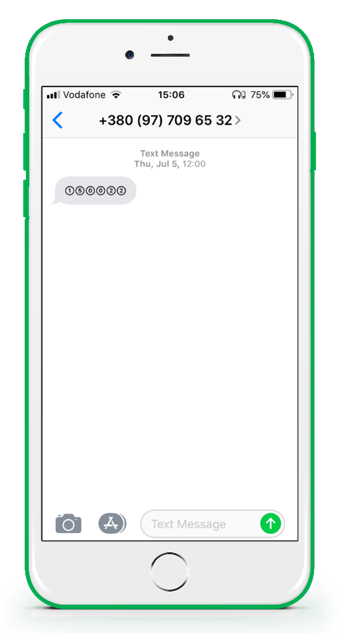
Using this method, the entire difference in the price of delivery goes into the hub’s pocket. All that the operator can do is to block the traffic and wait until it comes to the legal channel while dealing with irate clients’ complaints.
Problems of communication in the A2P market
To be the master of its network, an MNO must have the ability to not only trace the A2P traffic, immediately detect leakages and block grey routes, but have a communication channel with all the services generating it.
Another typical case:
Because of manipulation, a user couldn’t receive SMS with a password to verify a transaction. When the user contacted the support staff of the payment service, he received a standard answer — “Please get in touch with your mobile operator.” The operator checked and informed the user that there had been no messages for the user and suggested “contacting the service.” Users often find themselves caught in this never-ending loop between the enterprise and the MNO.
The problem is unlikely to be solved quickly — clients will stay dissatisfied, and operators will continue receiving messages via grey routes eventually leading to a loss in both revenue and reputation.
Sergii Sushchenko, Head of Pre-Sales Division
“Many operators are facing this problem — technically they can block such manipulated messages, but only after they make sure, that there are no restrictions in terms of contracts with partners.”
The way for an MNO to uncover and immediately shut down any grey route is to work together with an international messaging provider to bring the traffic via authorised route. Such companies, besides being able to follow traffic and examine different data waves in real-time, tend to have contracts with many enterprises generating A2P messages.
Unlike MNOs, they have direct communication with international businesses and can quickly direct any problem to the right department responsible for traffic.
Setting the right SMS Firewall ruleset
Figuring out the right ruleset to efficiently block messages from grey routes is another delicate problem. One extra symbol is enough to trigger blockage of the entire legal traffic.
It is crucially important for an MNO to know the functionality of its SMS Firewall, to be able to apply various rules for different traffic sources and create blocking, if not by all, then by important message parameters like: “sent from”, “recipient”, “content”, combined with logic primitives and regular expressions.
Here is an example of Amazon standard ruleset template
______ is your Amazon verification code
______ is your Amazon security code.
______ is your Amazon login OTP. OTP is confidential. For security reasons, DO NOT share this OTP with anyone.
Where “______” is any numeric value.
An MNO can implement a simple rule to block traffic from Amazon by “Amazon & (code OR OTP)”: But implementing this rule carries the inherent that legitimate traffic that is not relevant to Amazon might also get blocked:
____ code (OTP) for your transaction at Amazon Pay
Correct SMS Firewall ruleset for Amazon looks like this:
- [SMS should start with 6 digits of the password] and then with “is your Amazon” pattern
- SMS should also contain keywords (verification code) OR (login OTP)
On the OpenMind Networks Traffic Control platform, the condition for the message blocking rule set for Amazon will be as follows:
regmatch(“^[0-9](6) is your Amazon”,msg) && (regmatch(“verification code “,msg) || regmatch(“security code “,msg) || regmatch(“login OTP “,msg))
The rule should be applied to all unauthorised sources of A2P traffic!
Of course, to monetise A2P traffic, an MNO needs to know such key features for all types of messages from services, considering the languages used.
In this instance, MNOs meet several challenges when moderating rulesets:
- not knowing keywords for certain services
- not knowing how their traffic is currently being delivered
- inability to monitor traffic from each service separately
To establish and maintain an effective, up-to-date SMS Firewall ruleset, MNOs partner with reliable A2P messaging companies, which can look for inconsistencies and surges, follow traffic and examine different data waves in real-time.
Sergii Sushchenko, Head of Pre-Sales Division
“MNOs monitor only the traffic incoming from several OTT services, while at GMS we analyse international traffic to different regions and have established rulesets for all services generating A2P messages.”
Takeaways
Just installing an SMS Firewall is not enough to stop unfair hubs from manipulations or plug revenue holes in an operator’s network. This instrument needs a professional team of technical specialists, analysts, lawyers, and managers to make it work full throttle.
Global Message Services is always there to ensure you’re using the right tools and have reasonable processes in place to claim that you have a secure and stable SMS Firewall ready to take on whatever comes your way. Talk to an expert today!

