A good SMS firewall is essential to securing a mobile operator’s network and properly managing its traffic. But what makes a good firewall? At their recent Global Strategy Review event in Cadiz, ROCCO shared some of the results of a recent study on A2P monetisation. They suggested that MNOs are often most concerned with the ability of their firewall to detect SIM boxes, its pattern recognition capabilities, and the relevant market knowledge of those powering their firewall solution.
This is understandable. SIM boxes can create a real drain on an operator’s revenue, whilst being tricky to spot. A firewall also needs to be able to sort traffic properly: if it misidentifies A2P messages as P2P the operators fall prey to the dreaded grey routes. And clearly you want the team behind it to be experts in what they do.
SIM box detection
This particular threat has been around for a while, but still ranks highly on MNOs’ list of concerns. SIM boxes started life as a way to route calls between countries’ networks without going through official international termination points. Instead, unscrupulous partners route calls using VoIP, sending them to SIM boxes filled with SIMs from an uncontrolled domestic neighbor network, which then connect the call to that network at local rates.
The same principle applies to SIM box fraud over SMS, which is particularly prevalent in emerging markets such as those in African nations, or those with high interworking charges and cheap (or free) local messaging rates. Rather than paying to route international messaging traffic via the proper channels, and thereby accruing interworking fees, fraudsters route traffic over IP channels to a SIM box. Again, the SIM box connects at a local rate and the fraudster pockets the difference.
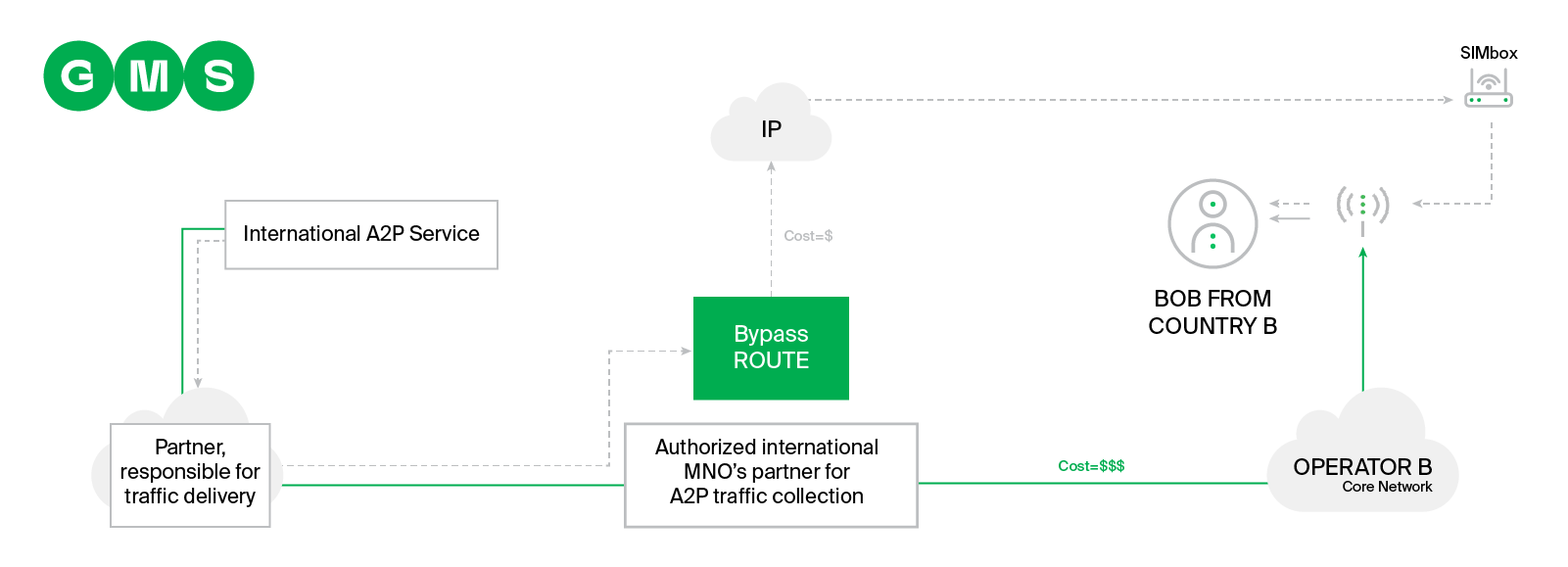
This is especially bad given the free messaging often bundled with pre-paid SIMs, the weapon of choice in this scenario. Prepaid SIMs don’t require any billing information, making it harder to trace the perpetrators.
Compounding this is the versatility of SIM boxes. When a card is identified as part of a SIM box and blocked, it can simply be removed and replaced. Some fraudsters even use “Human Behaviour Simulation” to trick attempts to track them.
- They might move cards from one box to another to give the impression the user is moving.
- They can rotate SIMs in a particular box so they are not in use all the time, which looks suspicious.
- Some SIM boxes transmit MO/MT voice calls and SMSs between their SIMs, or even access the internet in order to mimic human usage.
The challenge then is ensuring that the firewall is responsive to this (sometimes literally) moving target. That’s why GMS advise that a firewall should monitor all possible SMS MT routes and constantly analyse the traffic passing through it. The key is regular testing and reporting, analysing how traffic flows through the whole network in order to detect suspicious traffic. GMS looks at the operator’s network and the surrounding mobile ecosystem and compares expected verses actual traffic. Then the network is stress-tested to determine where and how messages are actually being delivered. Based on the results, GMS updates its technical solutions or provides recommendations to help operators control illegitimate messaging routes.
Pattern recognition
Possibly the most talked about problem for MNOs, in terms of their control over their own revenue, is grey routes. And a core component of this problem is the difference between International A2P and National A2P/P2P messaging, and the asymmetry of their pricing. Naturally, operators want their firewall solutions to be able to accurately and consistently differentiate between the two.
The problem is that, if you know how, it’s comparatively simple to manipulate a message’s sender ID and content to disguise A2P as P2P, so simply filtering the two into different routes isn’t enough. To properly identify A2P traffic might require comparing messages’ metadata or looking harder at where they are coming from. Whilst analysing the network after-the-fact can help catch these details, it is less than ideal on an on-going basis. You want a firewall that can identify suspect messaging traffic as it arrives, reducing the amount that slips through to a bare minimum. This is where pattern recognition comes into play.
“I’d like to believe that we know our business area in detail and use this knowledge on behalf of our MNO partners,” Sergii Sushchenko, GMS’ Head of FW Operations and Network Testing Division
Knowing how existing threats work, understanding the wider messaging ecosystem, and a consistent policy of analysis and adaptation are the cornerstones of recognising grey route patterns. They are also areas in which GMS excels. A full analysis of the network environment reveals potential bad actors, and ongoing monitoring finds and eliminates revenue leaks whilst preventing new ones from forming. Furthermore, GMS and its technology partners are always devising new ways to enhance this, from something as simple as a good reporting tool, to AI-driven pattern recognition in real time. By training a machine to distinguish between valid A2P traffic and unknown/suspicious patterns potential grey routes could be identified, flagged, and resolved as they emerge. That’s the ideal pattern recognition, enhanced by testing and traffic analysis results.
Knowledge
These solutions don’t mean much without the ability to implement them. Operators expect a degree of experience and expertise commensurate with the threats they face. This goes beyond just knowing how to set up the firewall, but also the background knowledge necessary to plan and implement it. As we discussed above, this means considering the business and networking landscape surrounding an operator.
Sergii Sushchenko, GMS’ Head of FW Operations and Network Testing Division, says the key is having a “detailed network picture, where all possible traffic sources are highlighted together with possible traffic bypass options.” That way GMS and operators can create a clear plan of action. This, he argues, goes hand-in-hand with an awareness of the broader market and infrastructure. Not only do you ensure clear visibility of traffic origins (“sometimes, despite traffic being analysed by the Firewall, you’re unable to understand who really sent this traffic … [you need to] make a clear plan of how to cover and monitor all potential threats”) but this also allows you to “discover alternative tools, which could improve traffic visibility and network control.”
GMS offers holistic, turn-key solutions that account for the big picture, understanding the operator’s market, traffic, and relations with their other partners. GMS’ firewall solutions are part of a big-picture approach that makes the most of the available technology and the insights of GMS’ experts.

